POC Google Authenticator Project
A recent comment I received made me go back and revisit my “Implementing Google Authenticator in PeopleSoft” post where I discuss the code involved to get Google Authenticator working in PeopleSoft. Revisiting this post made me realize that I never actually shared the source App Designer project with the community. I would like to use this post to share the plug and play POC project that I use to enforce component-level 2FA with Google Authenticator in PeopleSoft applications.
Disclaimer: I will admit that the design and logic of parts of this project are a little sketchy. I created this POC project on the fly a while back with the intent of revisiting it to clean it up. I began to shift my research efforts from component-level 2FA schemes to field-level 2FA schemes and I never took the time to revisit this project. I can certainly create a better version of this project if there is interest.
With that disclaimer out of the way, this post will contain the steps to install the project and get it up and running. If you would like more technical details of how the project works, then check this post out.
Add psGAuth.jar to class directory in your PS_HOME on the app server (%PS_HOME%\class\psGAuth.jar) and bounce the app server with a cache clear.
UPDATE 2/22/18: The provided JAR file does not function properly in PeopleTools 8.56 as it it dependent on an older version of Apache Commons Codec. See comments for more details.
UPDATE 3/30/18: Check out the post Validating Time-Based One-Time Passwords if you do not want to have the custom Java class (psGAuth.jar) app server dependency. That post demonstrates an alternative method to validating TOTPs that does not require an app server dependency.
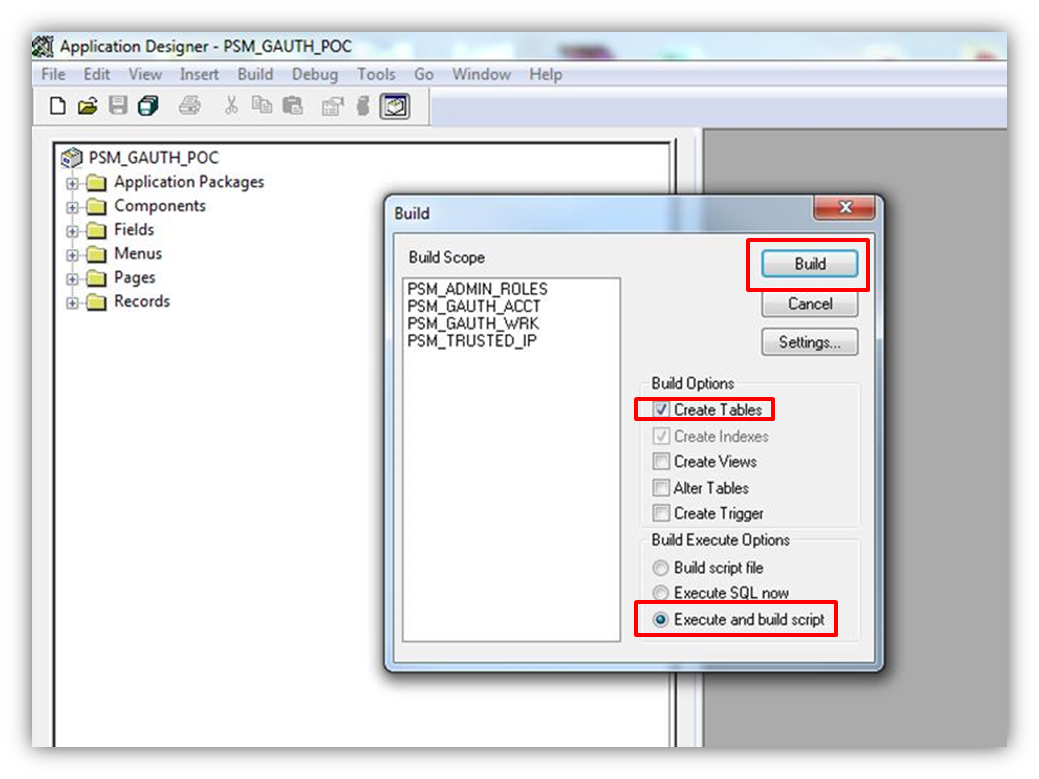
Import the App Designer project into App Designer and build the project.
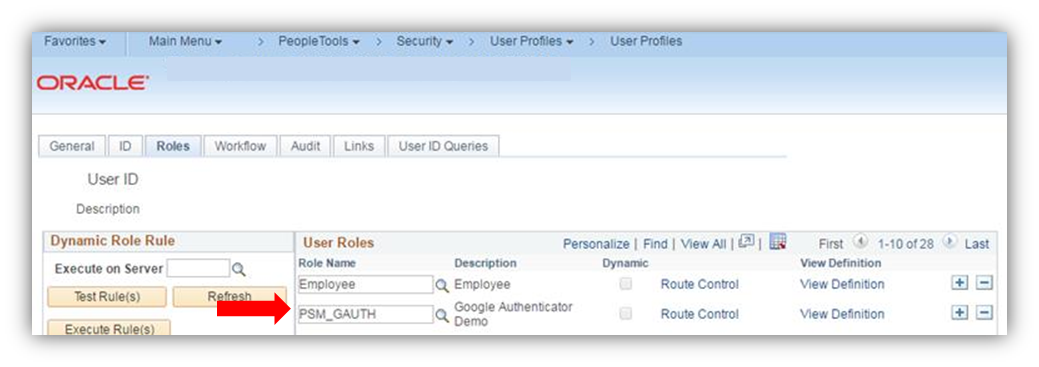
Login to the PIA and assign a user the provided PSM_GAUTH role.
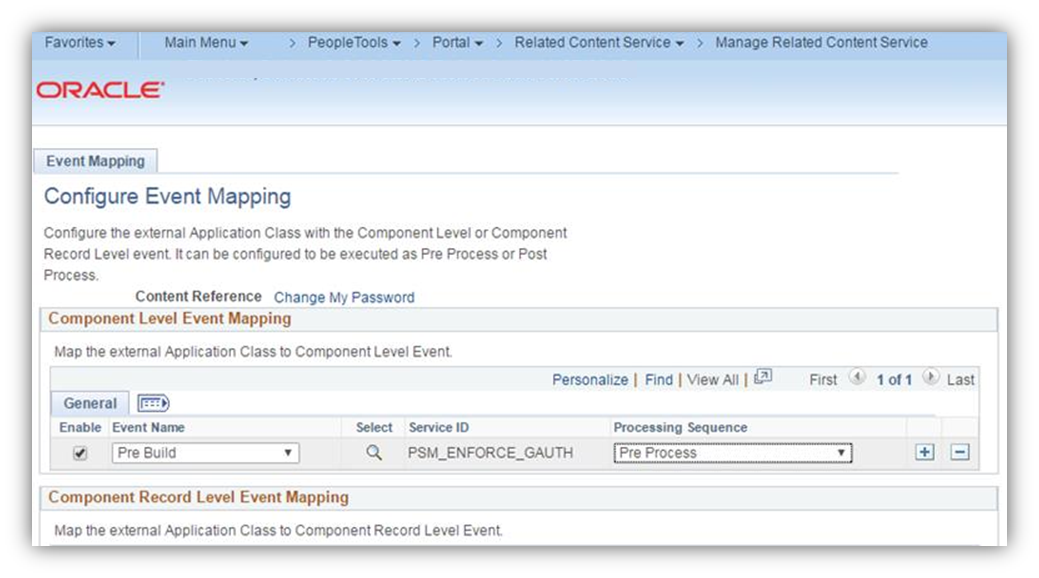
If you are on 8.55+ Tools, then you can make use of event mapping to achieve the 2FA functionality. To do this, map the provided related content service named PSM_ENFORCE_GAUTH to the Pre Build event of a component that you want enable 2FA on.
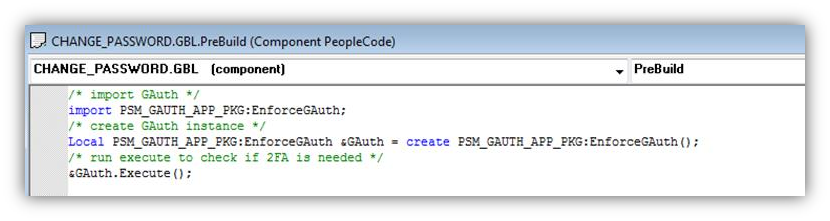
If you are not yet on the 8.55 Tools, then you will have to customize the Pre Build event of the component that you want to enable 2FA on. I highly recommend getting on 8.55 to avoid this type of customization, but you can paste the following code into the beginning of the component’s Pre Build event to enforce 2FA:
/* import GAuth */ import PSM_GAUTH_APP_PKG:EnforceGAuth; /* create GAuth instance */ Local PSM_GAUTH_APP_PKG:EnforceGAuth &GAuth = create PSM_GAUTH_APP_PKG:EnforceGAuth(); /* run execute to check if 2FA is needed */ &GAuth.Execute();
For example:
Now when you navigate to the 2FA-enabled component as the user with the PSM_GAUTH role, then you should be prompted to do a one-time setup for Google Authenticator. The next time you access a 2FA-enabled component, you will be prompted to input a Google Authenticator TOTP unless you possess a valid 2FA cookie (more on this below).
Important Consideration:
The code is written to issue a 2FA cookie after a successful Google Authenticator challenge. On subsequent requests to 2FA-enabled components, the code will not challenge a user for 2FA if they possess a valid 2FA cookie in their browser. I applied this logic to the project to demonstrate a general idea of how you can go about satisfying potential usability requirements. I strongly recommend that you evaluate this practice to determine if you want or need your system to allow for this sort of 2FA bypass mechanism. If you decide to allow for the possession of a cookie to bypass 2FA, then please DO NOT rely on the way that it is coded in the project to achieve this functionality.
Included in this project are some objects to make the 2FA process more configurable. This includes things like setup tables to house which PeopleSoft roles to enforce 2FA for and which IP address ranges should be trusted to bypass 2FA. Similar to the 2FA cookie bypass mechanism I described above, I included these mechanisms to expose the idea of how make the 2FA process more accommodating to usability requirements.
If you are interesting in implementing this project feel free to download and give it a try, but please keep in mind that it is merely a proof of concept of how you can go about enforcing component-level 2FA. Please feel free to ask any questions that you may have about this project.
Comments
Paul Van Lankvelt
Thanks Colton, I will try it out.
Sivananda Koya
Hi Colton,
Your post is amazing.I have practically tried it out and it is working seamlessly with minor changes. A couple of things I did after importing your project to make it work in my case.
That’s it. With those minor changes I was able to use google authenticator functionality.
Thanks a lot for this wonderful post
Sandeep
Nice Article Colton , worth a shot .. Just 1 question from end user perspective they can still use the install Authenticator App on the phone and when approved users will be in ?
Colton Fischer
Hi Sandeep, I am not sure if I understand your question exactly. End users have the ability to install the authenticator app on their device at anytime. You can enforce some or all of your users to use the authenticator app to access your system. You can enforce who, when, and where you want a user to have to use the authenticator app to access your system.
I am sorry if I did not answer your question, if you could provide more details that would be great.
Dan
Love this project. I started implementing it on several of our pages and it worked great! However, this is an issue with PeopleTools. Apparently if you implement event mapping and make changes via an app package PC, then the page activate (and also pre and post build PC I believe) PC does not fire at all. Oracle acknowledges the bug and states it will be fixed in 8.55.12 or 8.56. Unfortunately, neither of those are happening anytime soon (we’re on 8.55.06). Document ID 2213313.1
Colton Fischer
I am glad you are making use of this project. Thank you for sharing your experiences and for providing us with the Doc ID. I think I might’ve experienced this same bug on the Change My Password page where the user description does not get populated when I have event mapped code.
Jared
Hi Colton,
Sweet post! I imported the project but I can’t find the navigation to the configuration page. Can you provide the navigation? I have already applied permissions to my user ID.
Thanks, Jared
Colton Fischer
Hi Jared. After importing the project and assigning the permissions, the only configured page that is needed is the delivered “Manage Related Content Service” page. The path to this page is Main Menu > PeopleTools > Portal > Related Content Service > Manage Related Content Service. Here you will map the PSM_ENFORCE_GAUTH service to the Component(s) that you want to enable 2FA on. This should be the only configuration that is needed to get this to work. Please let me know if this answers your question. Also let me know if you are having any issues getting this project to work. I’d be more than glad to help you get it working.
Steve
Hello Colton, If I load and test the POC Google Authenticator Project (PSM_GAUTH_POC) is there a prerequisite of implementing any other of your Two-Factor Authentication projects; i.e., Setting up Two-Factor Authentication (PSM_2FA_POC) and/or Using the Event Mapping Framework to Enforce Two-Factor Authentication (PSM_2FA-EVENT_MAPPING_POC)? Are each of the projects mentioned considered standalone?
Thank you, Steve
Colton Fischer
Hi Steve. The project in this post is standalone. If you follow the steps in this post to install the downloadable project and configure a component for 2FA, then it should just work. Please let me know if the steps in this post are not clear or if you have post-installation issues.
Andrew Crawford
Getting a error when clicking the “Setup Google Authenticator” button.
“Java Exception: java.lang.NoClassDefFoundError: org/apache/commons/codec/binary/Base32: during call of psGAuth.GetKey. (2,763) PSM_GAUTH_WRK.PSM_SETUP_GAUTH.FieldEdit PCPC:371 Statement:6
The noted Java error was thrown during a call of the given method.”
Colton Fischer
The org/apache/commons/codec/binary/Base32 class existed in the delivered Java on the app server that I developed this solution in. This was on an app server running Tools 8.55. Which PeopleTools version are you running? Does the %PS_HOME%\class\ directory on the server contain all of the delivered JAR files? If this directory has been altered to where the org/apache/commons/codec/binary/Base32 class was removed, then that could be why this is happening.
Andrew Crawford
We are on Tools 8.56 and we have not changed any of the delivered class files.
Andrew Crawford
8.56 comes with commons-codec-1.2. This does not seem to include Base32, only has Base64.
Andrew Crawford
Adding commons-codec-1.11 to the server seems to resolve the issue.
Colton Fischer
Thank you for sharing this information, Andrew. I updated the post with the details that you provided.
Andrew Crawford
Download link for the library. https://commons.apache.org/proper/commons-codec/download_codec.cgi The library will need to be placed in the same CLASS folder as the project’s jar file: (%PS_HOME%\class)
Andrew Crawford
Had to do this as well. Once the now mentioned library is added, this works great.
Thanks for the post, it has been really helpful.
Leave a comment
Your email address will not be published. Required fields are marked *