Two-Factor Authentication in PeopleSoft
This post is to document my two-factor authentication (2FA) project that I have implemented in PeopleSoft. This project was done because there was a desire to add an additional layer of security to the application without having to worry about the costs associated with a vender-supplied 2FA solution. A customization like this would seem to be somewhat infeasible to build in-house, but leveraging some of Oracle’s delivered functionality coupled with a well thought-out design, made this project’s implementation quite simple. This is relatively speaking of course, after all, this project does add an entire new step to the delivered PeopleSoft authentication process. I am only going to talk about the requirements, specifications, and design in this post as well as provide a short demo. I am writing a tutorial here that shows the steps on how to implement this.
| Requirements | Specifications | Design |
| Implement a 2FA process that is imposed on users upon successful login. | After successful username/password authentication, redirect users to an intermediate (custom) 2FA page to do the 2FA process before taking them to the homepage | Modify the Signon PeopleCode to do the redirect. Use the ResultDocument parameter of the SetAuthenticationResult function to redirect users to the 2FA page. |
| Initial implementation of this project should only enforce 2FA on admin-level users that are accessing the system from outside the enterprise network. | During sign on, the logic must conditionally redirect authenticated users to the 2FA page based on their PS roles and their IP address. | Make use of the IsUserInRole function and the RemoteAddr property of the %Request class to determine the user’s security access and location. |
| The enforcement of 2FA should be scalable in respect to user roles in PeopleSoft as well as login locations. | A custom page needs to exist in PS that will store PS roles and IP addresses that 2FA will be enforced on. The sign on logic must reference this data to determine whether or not to challenge users for 2FA. | Create a PS page with grids to house the roles and IP addresses that 2FA will be enforced on. Reference this data in the Signon PeopleCode. |
| Give the users the ability to receive time-sensitive codes to either their email or cell phone for the 2FA process. | On the 2FA page, prompt the user to receive a time-based one-time password (TOTP) to their primary email or cellphone that is stored in the database. Use a third-party SMS gateway the send the TOTP to the user’s cellphone. | Write an algorithm to generate TOTPs. Email the TOTP to the user’s primary email address using the MCFOutboundEmail class or send the TOTP to the user’s cellphone by consuming Clickatell’s SMS gateway web service thorough their RESTful API. |
| Provide functionality for users that frequently login from the same location to not have the do the 2FA process every time they login. | Provide an option on the 2FA page to “Remember This Location”. Use a cookie-based solution to keep track of users that have previously performed 2FA from that location. The cookie’s uniqueness should be based off of user attributes and location. | Use the CreateCookie method of the %Response class to store a cookie to the user’s bowser. The cookie’s contents will be a hash of the login IP address along with user-specific attributes. |
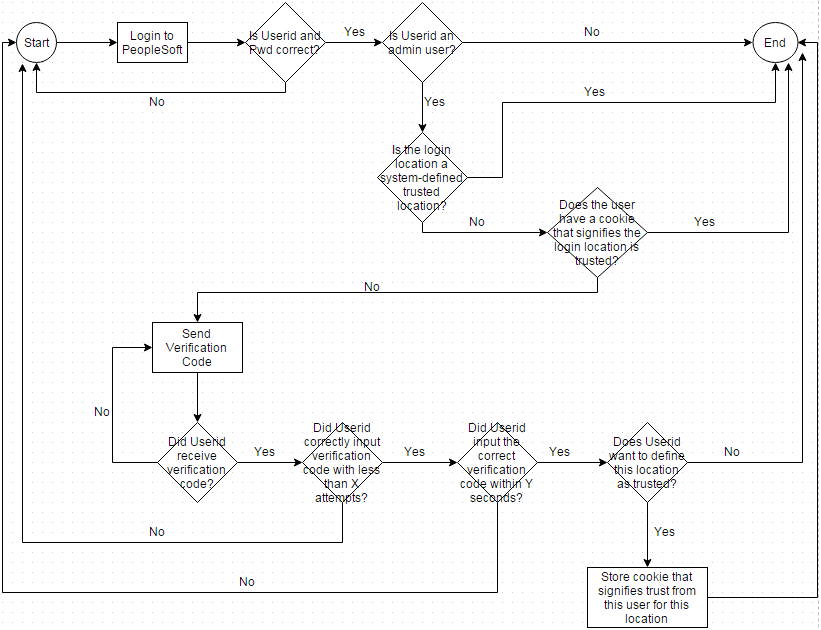
Here is the flow of the authentication process. The start is the login page and the end is the home page.
Here is a short video demonstration of this two-factor authentication solution for PeopleSoft.
If you are interested in the details of how to implement this project, then go here to view the tutorial.
Comments
#55 – 2FA and Event Mapping w/ Colton Fischer
[…] 2 Factor Authentication & Event Mapping @ 4:15 […]
AB Krishna
Thank you for the blog with so much of details - I am implementing your solution for our self serviice users After the user is authenticated , I am redirecting the user to custom “2 factor authentication” page.. This is happening from part of sign-on peoplecode func-lib . We see some body can interject/hack and bypass 2 factor page (with the url manipulation) . Is it possible to add a role for self service user using Peoplecode only after complete the 2 factor page successfully (until that time user has only access to 2 factor page only) I appreciate your input/comment
Colton Fischer
Hello. I believe I exchanged comments with one of your colleagues regarding this issue. As you have discovered, this technique of enforcing 2FA at the PeopleSoft login not longer behaves in a secure manner as it did in older Tools versions. With this being said, I do not recommend using this solution as a protection measure for application access.
As for assigning/revoking Roles in the 2FA process this should work in theory. I have never tried this though. You would just need to be sure that when you revoke the Role that gives the user broad access, then you need to revoke it in the Sign On PeopleCode before the call to SetAuthenticationResult and not on the intermediate 2FA page. I think doing something like this would allow this technique to behave like it did on older Tools. What you would be aiming for is for the ResultDoc redirection technique to behave like the Password Expired functionality does in the Sign On process. See the PasswordExpired parameter description for the SetAuthenticationResult function in PeopleBooks. In the description it states: If this value is specified as True, the user is allowed to log in, but is able to access only a limited portion of the system: just enough to change their expired password.
I’d be interested in hearing how this works out for you if you decide to go this route.
AB Krishna
Colton - I appreciate for your input (YES, I report to Kim, to whom you replied on this matter) . I was just thinking the same to revoke in the SIgn On peoplecode. We are discussing further and I shall share what approach we are taking and the results
Leave a comment
Your email address will not be published. Required fields are marked *